Install and Setup Burp Suite Proxy & Certificate with Java Application

This article demonstrates how to configure the Burp Suite certificate for Java applications.
Introduction
Java applications sometimes bypass global proxy settings, which means that setting up a proxy and importing the Burp Suite certificate may not be sufficient to intercept HTTPS traffic.
This article will guide you through setting up your Burp Suite proxy and certificate with a Java application to intercept HTTPS traffic effectively.
Environment
- A freshly installed Windows 7 with Internet Explorer;
- A Java application;
- Firefox and Burp Suite Pro installed;
- Burp Suite certificate imported into Firefox and IE.
Preparation
Install Java Environment
Navigate to the Java official website to download and install Java.
Restart Computer
Ensure that all configurations take effect by restarting your computer.
Setup Burp Suite Proxy & Certificate with Java Application
Import Burp Suite Certificate
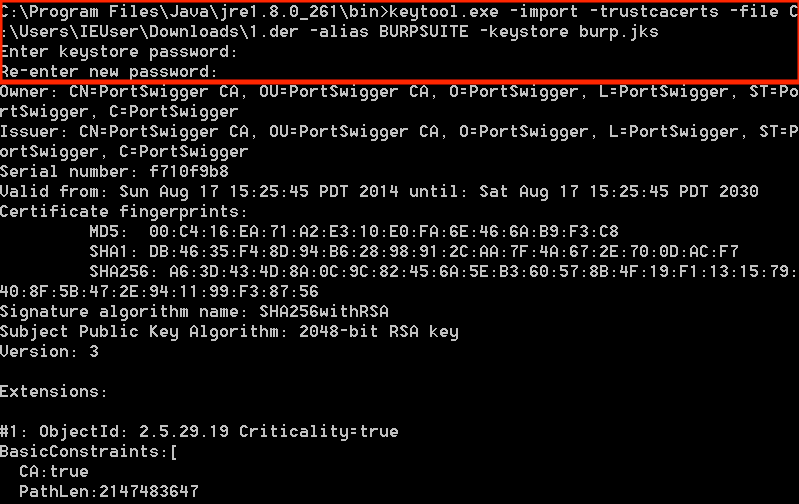
Open CMD and navigate to the Java bin folder. Note that the version number “jre1.8.0_261” may vary.
|
|
Execute the following command to import the Burp Suite certificate into the Java KeyStore using KeyTool, a command-line utility that manages keys and certificates.
|
|
When prompted, provide a password for the KeyStore. I used “123456”. Remember this password as it will be required later.
To verify the certificate has been imported successfully, execute the following:
|
|
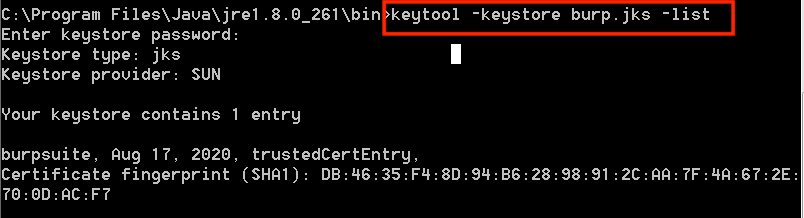
You have now successfully imported the Burp Suite certificate into Java.
Setup Burp Suite Proxy
When launching your Java application, include the following parameters to ensure the application uses the specified KeyStore:
|
|
With these settings, you should be able to intercept HTTPS traffic using Burp Suite.